OPENING QUESTIONS: Suggest at least 3 ways/methods we experience everyday designed to keep our data safe online
OBJECTIVES: We have several today:
- I will be able to describe two factor authentication (and problems associated with that) after today's class
- I will be able to describe mathematically what makes up a strong password
WORDS FOR TODAY:
- Big Data - a broad term for datasets so large or complex that traditional data processing applications are inadequate.
- Moore's Law - a predication made by Gordon Moore in 1965 that computing power will double every 1.5-2 years, it has remained more or less true ever since.
- Field - A holder of unique data of a unique data type (For example an AGE field contains integer data that stores a person's age. A field named FNAME would store character data that stores a person's first name
- Record - A "Row" of data related to a specific topic. For example FNAME, LNAME, ADDRESS, CITY, STATE, ZIP would contain data relating to a specific person.
- Table - A "Table" of data contains a bunch of rows of data. For example a spreadsheet is a table of data.
- Data Types:int | long | boolean | date | text
WORK O' THE DAY:
Worm - A computer program that self-replicates and is easily transmitted via the internet and especially via USB drives.
DOS/DDOS - Denial Of Service (or Distributed Denial of Service) attack occurs when a nefarious actor sends massive/repeated "Ping" or other commands to targeted servers in an attempt to crash that server
Phishing - A process where a nefarious actor(s) tries to gain access to a corporate/organization/personal computer or network by sending disguised email(s) loaded with nasty code to individuals in that organization
══════════════════════════
WORK FOR TODAY:
Let's further explore the idea of security online:
Passwords - Why do strong passwords always suggest a mixture of upper/lower case letters, symbols and letters?
Now think of that mathematically and try again!
How many letter combinations are possible for a 7 letter word if we ignore upper/lower cases but ignore numbers and symbols??
→ The answer is 26 (the number of letters in the alphabet) raised to the 7th power (the number of characters present
How many letter combinations are possible for a 7 letter word if we include upper/lower cases but ignore numbers and symbols?
How many letter combinations are possible for a 7 letter word if we include upper/lower cases and include numerical digits but exclude symbols?
How many letter combinations are possible for a 7 letter word if we include upper/lower cases, numerical digits and all the symbols found across the top of our keyboard?
So even a simply (letters only) password would *seem* to be relatively safe since there are billions of character possibilities. Let's put that to the test HERE
Here's a password creating method that our MOST Gracious & Humble Librarian Ms Marten shared with us a few years back:
❖Come up with a phrase that is easy for you to remember.
➢Select a favorite song title, movie title, or book title
❖Then use the first letters of the phrase to create your password.
❖Substitute a number for a word if possible.
Example: The cat is out of the bag!
Password: Tciootb!
══════════════════════════
What is multi-factor authentication?
Why do we care?
But there are flies in the ointment (of course, aren't there always?) Read THIS
══════════════════════════
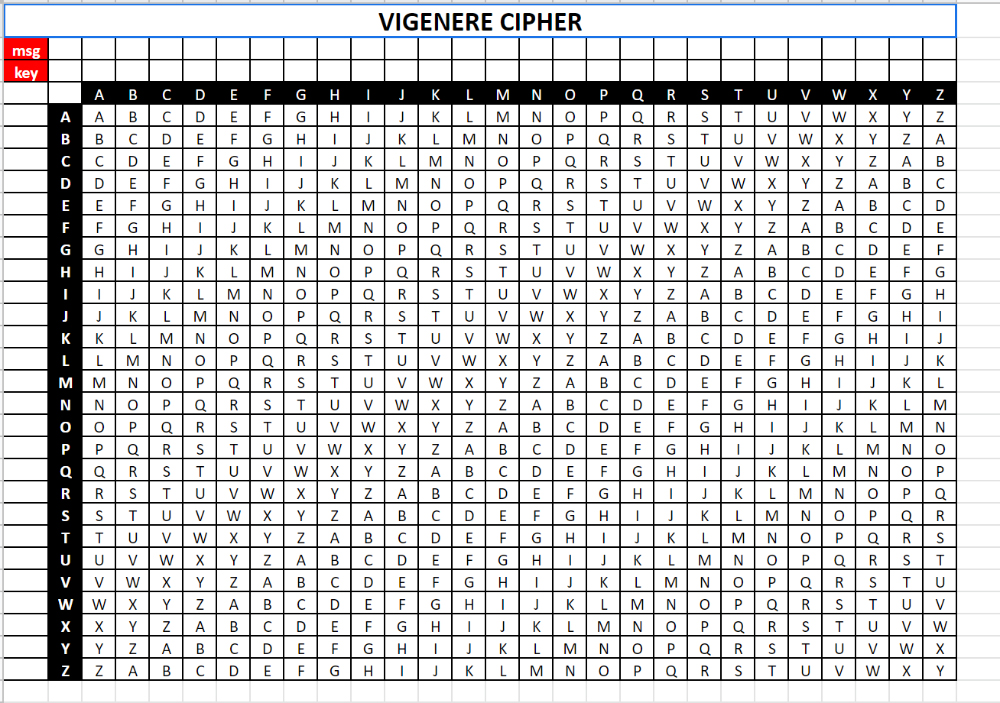
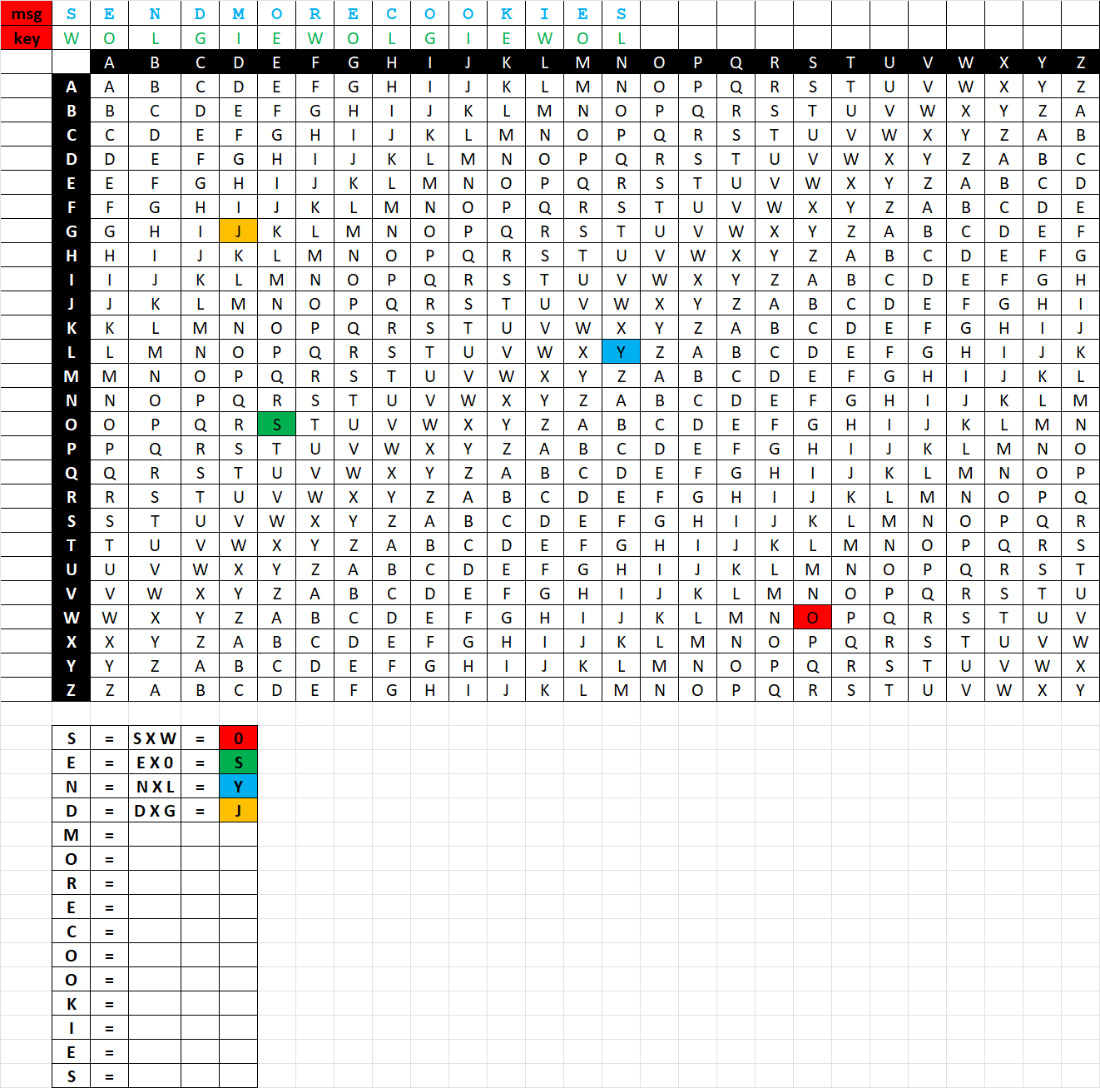
Here is an example of a simple substitution cipher -- which is fairly basic
Below is the Vigenere Cipher - an amazing tool that went unbroken for over 300 years (from the 16th 'til the middle of the 19th's century!!) (YIKES!)
Here's How!
Hopefully (? ACK! ?) you have the coded message you sent to a team mate using the Vigenere Squares method. (If you don't have that message, go HERE to create a new one) Type that message into THIS letter frequency analyzer.
Clearly these are ciphers that are not particularly helpful...
Here's an interesting thought... what is a book cipher? Can they be cracked?
I don't like to spend too much time playing these ciphers because, as fun and engaging as they maybe, they are all, WOEFULLY out of data:
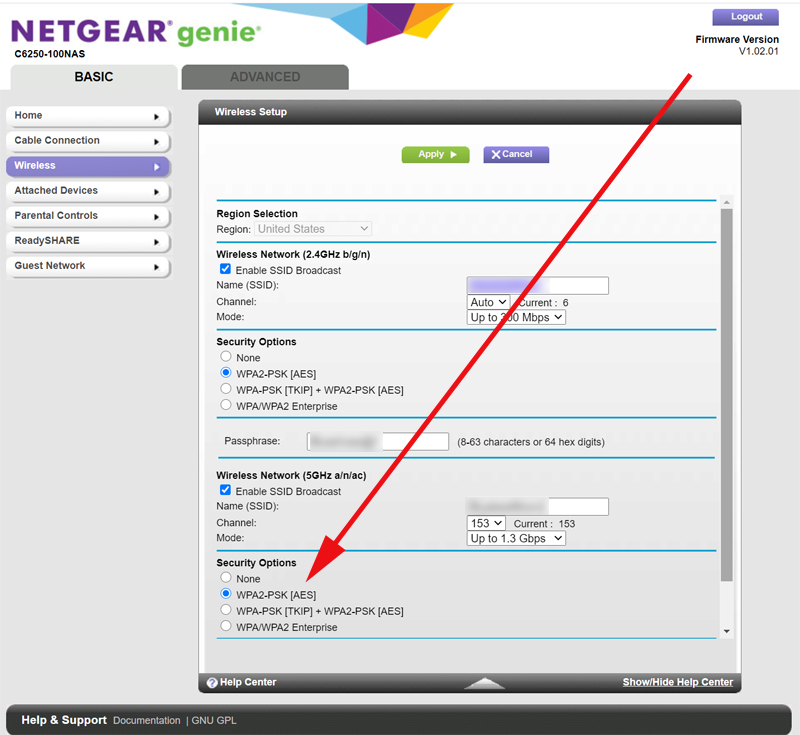
If you take a look at your wifi/router admin page (check with your folks FIRST, as always!) you'll see a dizzying set of encryption standards to choose from:
AES is kind of the "go to" standard these days.
Check out the rather astounding process that occurs in order to encrypt data using AES:
Let's have our MG&HTA lead us in conversation about that fairly *amazing* process!
Imagine... that process happens EVERY time data is sent out across the web!
You DO NOT need to know that process, just a general idea of how much work gets done to every packet (by the way, on what packet layer does that occur?)
For next time: Please provide an accurate, succinct contrast (how they are different) of Public Key Encryption and Private Key Encryption on 1, count 'em one, slide (images are encouraged) suitable for grading (*ahem*)
Please convert your slide to a jpg, png or similar image file so we can upload to a classroom media album
Best works will include:
- Clear and concise language easily understandable by everyone in the class
- The Goldilocks Standard very definitely applies here:
- Too much verbiage and your audience (that would be US) gets lost.
- Too little verbiage and your audience is left wondering
- NOT a copy-paste-change-the-words adaption of something you found online
Here's where it gets a wee bit dicey.
A public key is a key that is published that everyone can see. A private key is a key that only the individual holds.
Uh... yeah, but so what?
Does THAT statement help you understand what a private encryption key is or what it does?
Does THAT statement help you understand what public encryption key is or what it does?
You will find that this assignment, although short, will prove to tax your ingenuity and descriptive powers.
We will, once again, vote on the MOST impressive descriptors and the winner gets crowing rights